kubernetes Role Rolebinding ClusterRole RBAC
对于 Role、RoleBinding、ClusterRole、ClusterRoleBinding都可以使用在 user、serviceaccount、group上,使用方法相同只是参数不同。
Role
创建role资源:
kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml
yaml:
apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: pods-reader rules: - apiGroups: # 表示对API群组内的资源操作,"" 表示核心资源组,使用kubectl api-resources 第三列可以查看到 - "" resources: - pods verbs: - get - list - watch
示例:每个resources资源对象在各自的apiGroup的API组中拥有verbs操作方法。
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: kube-state-metrics rules: - apiGroups: [""] resources: ["nodes", "pods", "services", "resourcequotas", "replicationcontrollers", "limitranges", "persistentvolumeclaims", "persistentvolumes", "namespaces", "endpoints"] verbs: ["list", "watch"] - apiGroups: ["extensions"] resources: ["daemonsets", "deployments", "replicasets"] verbs: ["list", "watch"] - apiGroups: ["apps"] resources: ["statefulsets"] verbs: ["list", "watch"] - apiGroups: ["batch"] resources: ["cronjobs", "jobs"] verbs: ["list", "watch"] - apiGroups: ["autoscaling"] resources: ["horizontalpodautoscalers"] verbs: ["list", "watch"]
查看该资源:
]# kubectl get role NAME AGE pods-reader 26s ]# kubectl describe role pods-reader ... PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- pods [] [] [get list watch]
Rolebinding
创建rolebinding:
创建rolebinding时使用到的用户账号不同手动去创建。
kubectl create rolebinding reader-pods --role=pods-reader --user=qiyang
yaml:
apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: reader-pods roleRef: # 涉及到的role apiGroup: rbac.authorization.k8s.io kind: Role name: pods-reader subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: qiyang
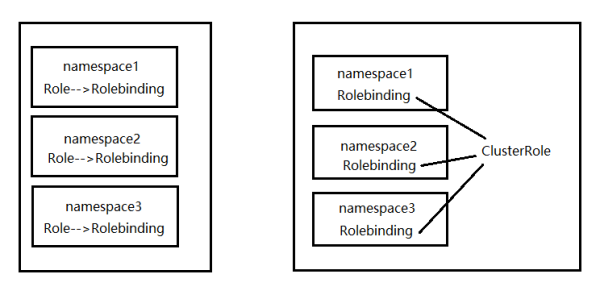
正常情况下,某个名称空间中一个role一个rolebinding,但是集群role也就是ClusterRole可以不限制于名称空间,各个名称空间的rolebinding来绑定ClusterRole这样可以不用为每个名称空间来单独创建一个role。
使用权限:
给新账号qiyang绑定了角色后就拥有了角色的权限,切换用户就可以使用新用户的权限了。
kubectl config use-context qiyang@kubernetes kubectl get pods
但是这个账号只拥有当前名称空间的权限,要想查看其他名称空间的pod需要定义其他名称空间的role并绑定,或者创建ClusterRole并用ClusterRolebinding 这样就可以拥有整个集群所有名称空间的访问权限了。
ClusterRole
如下图所示:让用户拥有集群级别所有名称空间的权限就要用ClusterRole+ClusterRoleBinding。
创建ClusterRole:
kubectl create clusterrole qiyangclusterrole --verb=get,list,watch --resource=pods,pods/status --dry-run -o yaml
--verb=* 用星号可表示全部权限
--resource=pods,pods/status 访问的资源类型 --resource=* 同样也可以用星号表示所有资源
yaml:
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: qiyangclusterrole rules: - apiGroups: - "" resources: - pods - pods/status verbs: - get - list - watch
yaml:用 * 表示所有权限
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: qiyangclusterrole rules: - apiGroups: - "" resources: - "*" verbs:
ClusterRoleBinding:
kubectl create clusterrolebinding qiyangclusterrolebinding --clusterrole=qiyangclusterrole --user=qiyang --dry-run -o yaml
yaml:
apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: qiyangclusterrolebinding roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: qiyangclusterrole subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: qiyang
Rolebinding 绑定 ClusterRole:
kubectl create rolebinding rolebindingClusterrole --clusterrole=qiyangclusterrole --user=qiyang --dry-run -o yaml
yaml:
apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: creationTimestamp: null name: rolebindingClusterrole roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: qiyangclusterrole subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: qiyang
权限验证
验证权限:是否有权限在某名称空间创建某种资源
kubectl auth can-i create deployments --namespace dev
例:是否有权限approve csr请求。
kubectl auth can-i approve csr
创建只读账号
实例:
创建 serviceaccount:
kubectl create serviceaccount clusterviewer
将 serviceaccount 绑定到view这个clusterrole:这里的view是k8s集群自带的只读clusterrole。
kubectl create clusterrolebinding clusterviewer --clusterrole=view --serviceaccount=default:clusterviewer
找到 serviceaccount 默认绑定的Token:
kubectl describe serviceaccount clusterviewer
输出:
Name: clusterviewer Namespace: default Labels: <none> Annotations: <none> Image pull secrets: <none> Mountable secrets: clusterviewer-token-fwq2n Tokens: clusterviewer-token-fwq2n # 在secrets资源中找这个token Events: <none>
查看token:
kubectl describe secrets clusterviewer-token-fwq2n
输出:
Name: clusterviewer-token-fwq2n Namespace: default Labels: <none> Annotations: kubernetes.io/service-account.name: clusterviewer kubernetes.io/service-account.uid: fc0d6ed6-4daa-4e47-90cf-c33abdf6d30d Type: kubernetes.io/service-account-token Data ==== ca.crt: 1017 bytes namespace: 7 bytes token: eyJhbGciOiJSU.......X3jv_xC6A # 这个token就有了名为view这个clusterrole的权限了
这个token可以用于浏览dashboard,也可以用来创建kubeconfig配置文件。
官方文档:
https://kubernetes.io/zh-cn/docs/reference/access-authn-authz/rbac/
