Istio Sidecar EnvoyFilter WasmPlugin
来源:原创
时间:2022-03-24
作者:脚本小站
分类:云原生
Sidecar:
用来定义某个Sidecar流量出入的。
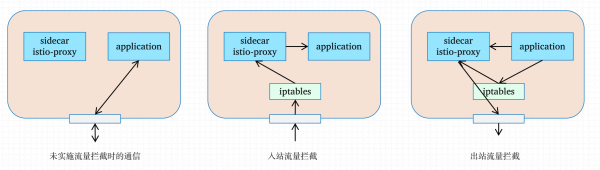
Sidecar:
apiVersion: networking.istio.io/v1alpha3 kind: Sidecar metadata: name: default namespace: default spec: ingress: - port: number: 9080 protocol: HTTP name: somename defaultEndpoint: unix:///var/run/someuds.sock egress: - port: number: 9080 protocol: HTTP name: egresshttp hosts: - "default/*" - hosts: - "istio-system/*"
Sidecar:
apiVersion: networking.istio.io/v1alpha3 kind: Sidecar metadata: name: partial-ip-tables namespace: prod-us1 spec: workloadSelector: labels: app: productpage ingress: - bind: 172.16.1.32 port: number: 80 protocol: HTTP name: somename defaultEndpoint: 127.0.0.1:8080 captureMode: NONE egress: - captureMode: IPTABLES hosts: - "*/*"
示例一:
apiVersion: networking.istio.io/v1beta1 kind: Sidecar metadata: name: client namespace: default # default空间下的sidecar的envoy侦听器 spec: workloadSelector: labels: run: client # 选择带有这个标签的Pod的sidecar的envoy上 egress: # 出站侦听器 - hosts: - "./*" # 当前名称空间下的所有服务都创建出站侦听器(格式:namespace/servicename) - "istio-system/*" # 在istio-system名称空间下的所有服务创建出站侦听器
示例二:
apiVersion: networking.istio.io/v1beta1 kind: Sidecar metadata: name: client namespace: default spec: workloadSelector: labels: run: client outboundTrafficPolicy: mode: REGISTRY_ONLY # 仅注册的服务可以出,其他流量都丢弃 egress: - port: # 只为满足下面条件的服务创建出站侦听器,其他的服务都不创建 number: 80 protocol: HTTP name: proxy - hosts: - "./*"
实例:接着上面几篇的实例,这个sidecar应用在名为client的服务上。
下面这个配置是仅注册的流量可以出去,其他出去的流量直接丢弃进入blackhole。
apiVersion: networking.istio.io/v1beta1 kind: Sidecar metadata: name: client namespace: default spec: workloadSelector: labels: run: client outboundTrafficPolicy: mode: REGISTRY_ONLY # 只有访问端口为8080且协议为http的流量可以出去 egress: - port: number: 8080 protocol: HTTP name: demoapp hosts: - "./*"
应用sidecar前client中envoy的侦听器:
]# kubectl exec -it client -c istio-proxy -- pilot-agent request GET /listeners 932a1f2f-df89-4e0e-a661-f92e426d521b::0.0.0.0:15090 01246b9d-b814-4a7b-9bf2-c691937831a0::0.0.0.0:15021 10.96.204.80_15012::10.96.204.80:15012 10.96.204.80_443::10.96.204.80:443 10.105.56.24_443::10.105.56.24:443 10.99.143.236_31400::10.99.143.236:31400 10.106.32.122_443::10.106.32.122:443 10.99.143.236_443::10.99.143.236:443 10.99.143.236_15443::10.99.143.236:15443 10.101.185.70_443::10.101.185.70:443 10.96.0.1_443::10.96.0.1:443 10.96.0.10_53::10.96.0.10:53 10.103.44.131_443::10.103.44.131:443 0.0.0.0_9090::0.0.0.0:9090 0.0.0.0_15010::0.0.0.0:15010 0.0.0.0_15014::0.0.0.0:15014 0.0.0.0_80::0.0.0.0:80 10.99.186.117_80::10.99.186.117:80 10.103.231.91_80::10.103.231.91:80 10.96.0.10_9153::10.96.0.10:9153 0.0.0.0_8000::0.0.0.0:8000 10.106.250.70_14268::10.106.250.70:14268 0.0.0.0_16685::0.0.0.0:16685 10.104.246.237_80::10.104.246.237:80 0.0.0.0_20001::0.0.0.0:20001 10.99.143.236_15021::10.99.143.236:15021 10.108.57.115_3000::10.108.57.115:3000 10.106.250.70_14250::10.106.250.70:14250 0.0.0.0_9411::0.0.0.0:9411 virtualOutbound::0.0.0.0:15001 virtualInbound::0.0.0.0:15006 10.99.26.101_8080::10.99.26.101:8080 0.0.0.0_8082::0.0.0.0:8082
应用sidecar配置之后client中envoy的侦听器:
]# kubectl exec -it client -c istio-proxy -- pilot-agent request GET /listeners 932a1f2f-df89-4e0e-a661-f92e426d521b::0.0.0.0:15090 # prometheus的指标 01246b9d-b814-4a7b-9bf2-c691937831a0::0.0.0.0:15021 # 聚合的指标 virtualOutbound::0.0.0.0:15001 # 流量出口 virtualInbound::0.0.0.0:15006 # 流量入口 0.0.0.0_8080::0.0.0.0:8080 # 手动开放的服务
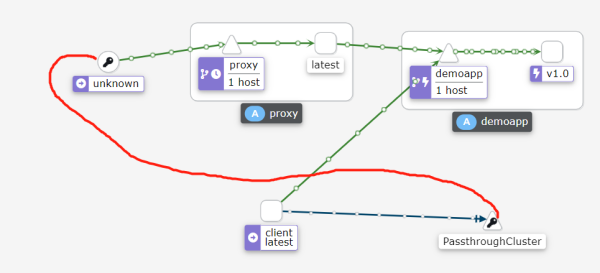
透传效果:
apiVersion: networking.istio.io/v1beta1 kind: Sidecar metadata: name: client namespace: default spec: workloadSelector: labels: run: client outboundTrafficPolicy: mode: ALLOW_ANY # 除了下面定义的端口和协议是进行代理的,其他流量直接透传,不通过envoy代理 egress: - port: number: 8080 protocol: HTTP name: demoapp hosts: - "./*"
如图:client访问的是proxy服务,透传就是没有经过envoy代理,所以envoy看不到流量是怎么出去的怎么进来的。
EnvoyFilter:
自定义Envoy的配置文件,直接修改Envoy的配置,有些功能在Istio的Api中没有,通过Envoyfilter可直接修改Envoy的配置。
WasmPlugin:
扩展sidecar(Envoy)的功能,它允许用户动态加载和运行 WebAssembly (Wasm) 模块,在不修改 Istio 或 Envoy 本身代码的情况下,实现自定义逻辑。
与 EnvoyFilter 的对比:
EnvoyFilter:
直接操作 Envoy 的底层配置(如监听器、集群、路由),功能强大但复杂。
需要深度了解 Envoy 的配置结构,易导致版本兼容性问题。
WasmPlugin:
更高层次的抽象,专注于 Wasm 模块的生命周期管理。
简化配置,更适合实现业务逻辑扩展。
未来可能逐步替代部分 EnvoyFilter 的使用场景。
